First Impressions using iStorage CloudAshur
I’ve been using iStorage devices for several years now and following the Sky News coverage of one of my data breach discoveries I was offered the opportunity to test out iStorage’s newest device; the CloudAshur Encrypted Cloud Module (don’t worry there aren’t any affiliate tags in this post [or anywhere on this blog for that matter]).
CloudAshur only supports Windows and Mac for now but the product has only just entered the market, I’m hoping they’ll support Linux/Chromebook soon.
Introduction: What is an Encrypted Cloud Module
The pitch for CloudAshur is that this module brings the security of local hardware encrypted storage to remote cloud, it does this by encrypting data locally using a “Common Criteria EAL4+ ready” microprocessor before sending the data onwards. The TL;DR of this is that the chip that does the cryptography has been evaluated to level 4 of the Common Criteria for Information Technology Security Evaluation.
Only other users with matching CloudAshur modules can decrypt the data, this combination of pin-protected local hardware and cloud credentials is what iStorage are referring to as “Five Factor” authentication;
- Something you have (the CloudAshur module)
- 7-15 digit Admin/User configurable PIN for the module
- Username and password for the iStorage cloudAshur Windows or macOS client app
- Where the data is stored (which cloud provider / path)
- Username and password for the cloud account
Arguably point 4 is simply “security through obscurity” and given that I’ve got hold of these devices because I demonstrated that putting data in a cloud storage service is no guarantee it won’t be found I’m somewhat skeptical of this point. That aside, I’m excited to see what we can do with these devices.
Getting started
CloudAshur modules are consumer devices so can be bought from the likes of Amazon, Scan.co.uk and Ebuyer.com. For businesses the usual VARs like Softcat are an option. https://istorage-uk.com/where-to-buy/ will have an up-to-date list.
As an Administrator deploying these devices you’ll need at least one of the two software products that compliment the hardware;
- Keywriter which can mass clone settings (User PINs, PIN policies, timeout policies, self-destruct PIN etc) but more importantly the cryptographic material that allows the devices to decrypt the remote data.
- Remote Management Console (Provides visibility of modules, allows remote kill etc)
KeyWriter is a one-off cost of £9.95 per device (cost breaks apply) with the RMC costing ~£19.95 per device per year (Cost breaks apply with device volume and term length).
Cost Examples (ex VAT)
Power User
| Item | Cost | Subtotal |
|---|---|---|
| Module #1 | £99 | £99 |
| Spare Module | £99 | £198 |
| Writer License x 2 | £19.90 | £217.90 |
SME
| Item | Cost | Subtotal |
|---|---|---|
| CloudAshur x20 | £1,980 | £1,980 |
| Spare x2 | £198 | £2,178 |
| Writer License x 22 | £ 214.50 | £2,392.50 |
| Remote Management x 20 (1 Year) | £416.90 | £2,809.40 |
Key Writer
Activating Key Writer is easy, you’ll receive an email containing a license key and an activation PIN. Navigate to https://cloudashur.istorage-uk.com/wp-dashborad/activate-keywriter-license/ and enter your details.
If everything goes to plan you’ll be good to go;

Remote Management
Remote Management is a little bit more complicated, as with KeyWriter you’ll receive an email with a license key and an activation PIN but upon activating the RMC you’ll receive another email with a different PIN (as well as a username and a password). This is your PIN, each user will receive their own PIN to use with the shared license key.
User Administration
Using Key Writer
The KeyWriter software requires the Activation PIN to be entered on launch;
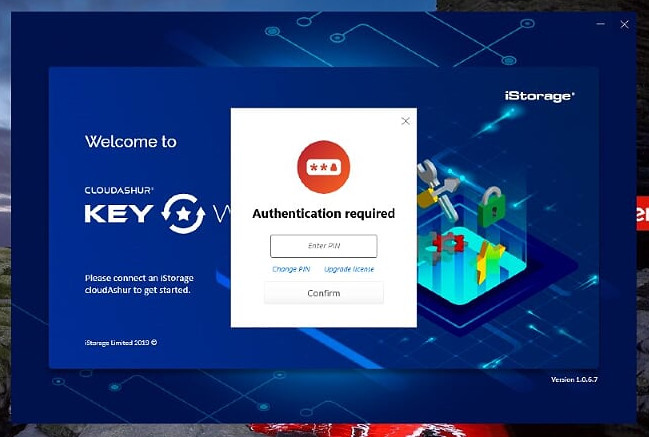
Once logged in you can specify any unlocked module as the ‘master’ device;
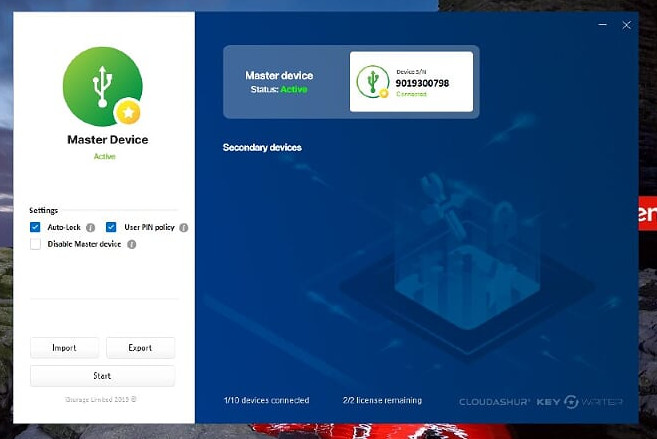
Unlock and insert the secondary devices and click the start button, the PIN config and cryptography data will be synced;
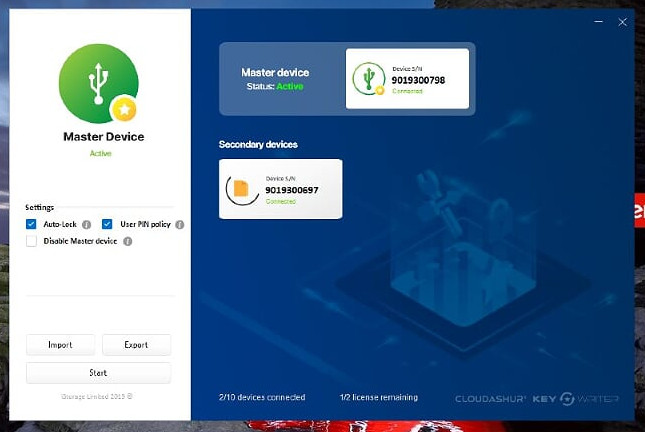
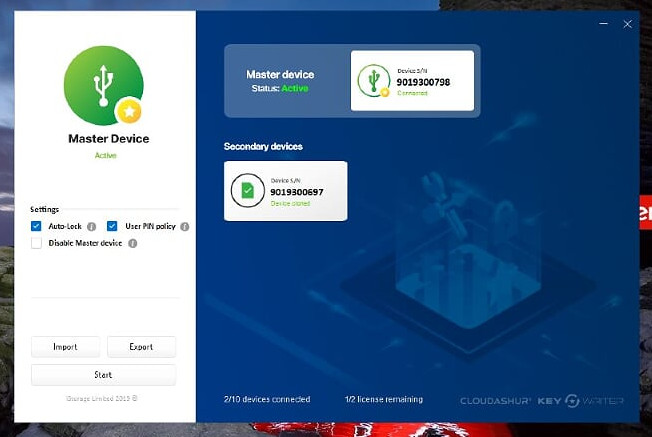
Now that the secondary device(s) are cloned they will be able to encrypt and decrypt data between themselves!
With a pair of modules that can share data it’s time to set about managing them.
Using the Remote Management Console
As per the documentation download the RMC software, install it, and then load it up. As we haven’t created an account yet we’ll need to select “Register” but because we entered some details when activating the license one needs to select “Existing User” in the next screen.
You must have a CloudAshur device plugged in and unlocked in order to “register”, USB modules are tied to an individual user account. Because we intend to use the RMC to manage the device that is plugged in we need to tick the “This device will be managed by Remote Management Console” checkbox and then enter the emailed PIN and license key.
Once done we’ll need to login with the username and password sent following the license activation and be greeted with the intial dashboard screen. From here you can create new users, set GeoIP blocking and more.
Using CloudAshur
Activating a new device as a user
Activating a new module as a user is quick and easy; unlock the device with either the user or Admin PIN, plug it in and load up the client app. Click ‘Registration’ and then “New User’, the device ID will already be filled in, complete the rest of the form (if this device is to be managed by the RMC ensure you tick the checkbox and complete the PIN and license key sent to you by the administrator), click register and you’re done!
Protecting Files
Once you’ve logged into the client application it will prompt you to select folders you want to protect, each time you write
to one of the selected locations you’ll receive a prompt asking if you wish to encrypt the file;
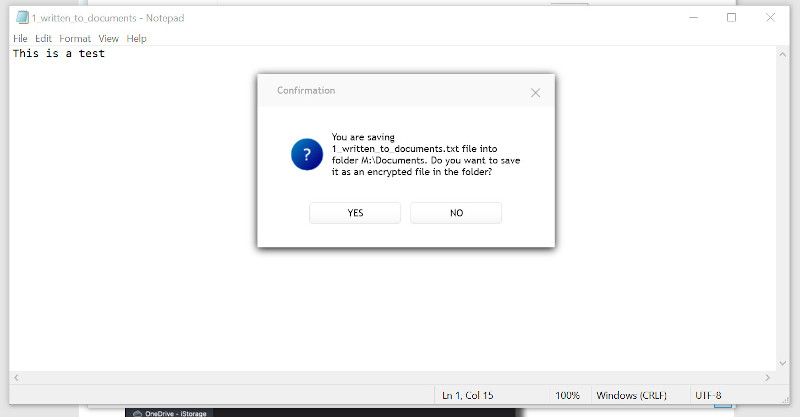
This highlights a flaw in the process; if a user writes / copies a file into a Cloud storage location, whether or not it is protected by CloudAshur, they are one click away from making a mistake.
There is no option within the UI to enforce encryption of all files copied to ~/Documents or This PC / OneDrive.
Case in point; this file was copied from This PC / Pictures and pasted to One Drive / Pictures, I was prompted to encrypt it and was able to choose no.
For a frictionless experience the CloudAshur client app creates an M:\ drive whose subfolders are the ones the user has chosen to protect. Writing to these locations via the M:\ drive ensures seamless encryption.
Performance
By using PowerShell and a quick snippet from StackOverflow I created an analog to Linux’s time and was able to generate some stats.
Local Storage
| File | Size | Copy without CloudAshur | Copy with CloudAshur |
|---|---|---|---|
| CentOS-8.1.1911-x86_64-boot.iso | 597Mb | 1.04 seconds | 427.57 seconds |
| CentOS-8.1.1911-x86_64-dvd1.iso | 7Gb | 23.35 seconds | 4022.41 seconds |
| War and Peace pdf | 20Mb | 0.038 seconds | ~6 seconds |
Writing to OneDrive
| File | Size | Copy without CloudAshur | Copy with CloudAshur |
|---|---|---|---|
| CentOS-8.1.1911-x86_64-boot.iso | ~500Mb | 193.96 seconds | 374.02 seconds |
| War and Peace pdf | 20Mb | 19.96 seconds | 23 seconds |
Cloud Collaboration (O365 and Google Docs)
Most of my clients make use of GSuite and Google Docs, unfortunately there doesn’t seem to be any support for Google Docs at the moment.
Likewise the web interface of https://office.live.com/start/word.aspx allows you to save documents to OneDrive but doesn’t result in the CloudAshur encryption prompt.
Copying a .docx file to OneDrive, and encrypting it results in the file being unusable in the web interface. I don’t have an Office license to test what happens when using or sharing documents using the native office suite.
Security
Each CloudAshur module is locked to the user that registered it so even if you manage to secure someone else’s CloudAshur module and their user PIN you can’t use your client credentials;
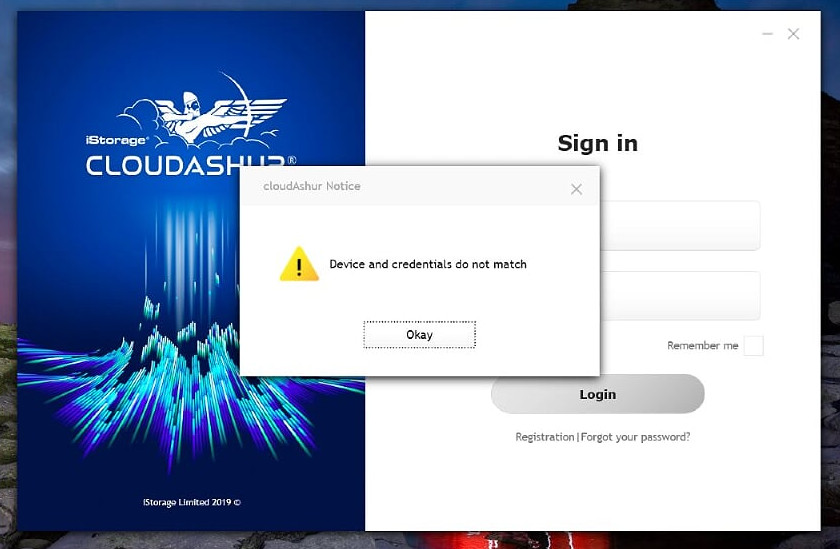
Likewise if you manage to gain access to someone’s cloud storage (in this case a shared OneDrive) and attempt to open the file with a CloudAshur module that hasn’t been cloned you’ll simply get garbage back;
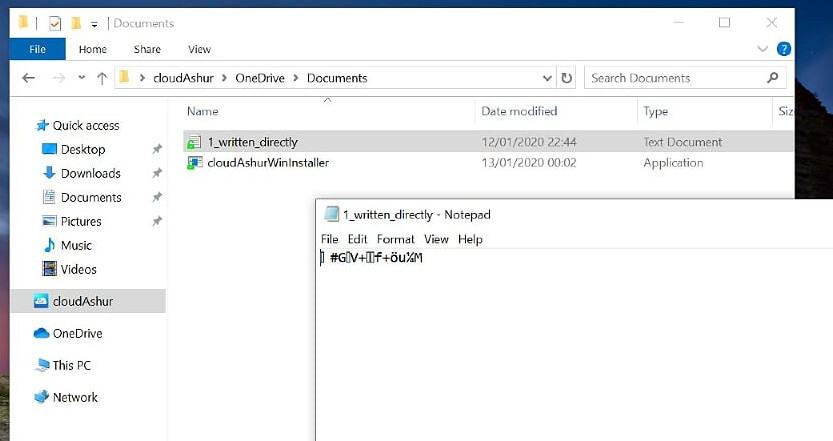 (It is worth noting however that the files are shown with a green unlocked padlock in the M:\ drive despite the fact that we subsequently can’t decrypt them)
(It is worth noting however that the files are shown with a green unlocked padlock in the M:\ drive despite the fact that we subsequently can’t decrypt them)
Conclusions
Users are Still the Weakest Link
As discussed in “Protecting Files” a user could accidentally choose “No” when pushing a file to Cloud storage and once done there is no Explorer context menu to encrypt this file after the fact.
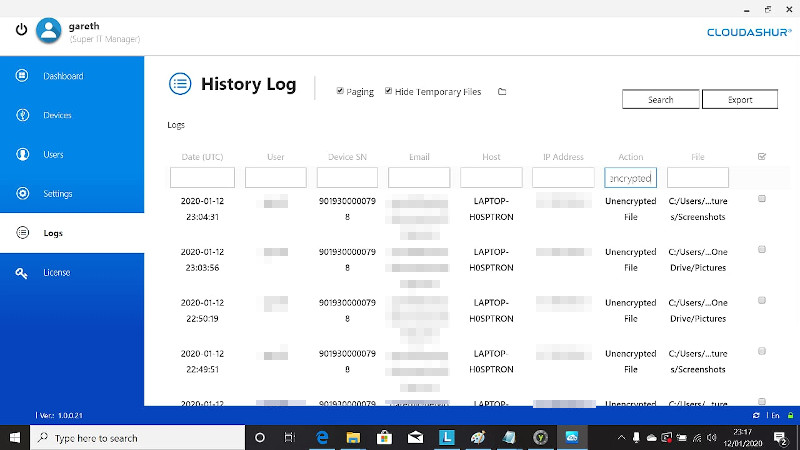
If you had the RMC then an Administrator can filter the logs for “Unencrypted File” but there doesn’t yet seem to be a way to have said logs streamed to a SIEM so the SOC can respond as required.
Confidentiality
Running strings on any CloudAshur encrypted file will tell you the serial number of the module that encrypted the file;
$ strings 1_written_directly.txt.ist
filename_encrypted = false
encrypt_mode = xts
software_version = 1.0.0
hardware_version = 1
file_extension = .ist
s/n = 9019300000798
Within a business this isn’t too much of a problem given that most of the file ownership or document metadata will also give this information away but once we move files into remote storage there is an opportunity for attackers / evesdroppers to build a profile of staff members for use with spearfishing etc.
As the NSA has said; metadata kills…
Wrapping up
All in all I’m impressed with this product, it’ll need to support Linux before I’d use it myself and it’d need to support Chromebooks / Google Docs before I advocated its adoption for any of my clients (to date all are GSuite users).
Even in the Windows world I think Administrators would want the ability to manage the folders through Group Policy and force the encryption of targeted cloud folders to prevent accidentally pushing unencrypted files to where they can be leaked. Whilst the cost isn’t prohibitive one does still rely on users to do the right thing to be fully protected.
For what it’s worth I did take a brief look at the server side of things (the client is very chatty) where I discovered a few minor issues;
- In an environment where DNS and TLS can be intercepted auto-updates can be misdirected and any download will automatically execute (once the user clicks “download” but an attacker can make the download mandatory or even totally automatic!)
- Certain endpoints exposed functionality / information that they shouldn’t (think debug UIs and/or swagger-like api-docs)
iStorage tooks steps to remediate both of these issues quickly.
When I get an opportunity I’ll push the GeoLocation restrictions and see just how hardy these aluminum cased wondersticks are!